info@oxtrabot.com
855-750-0004

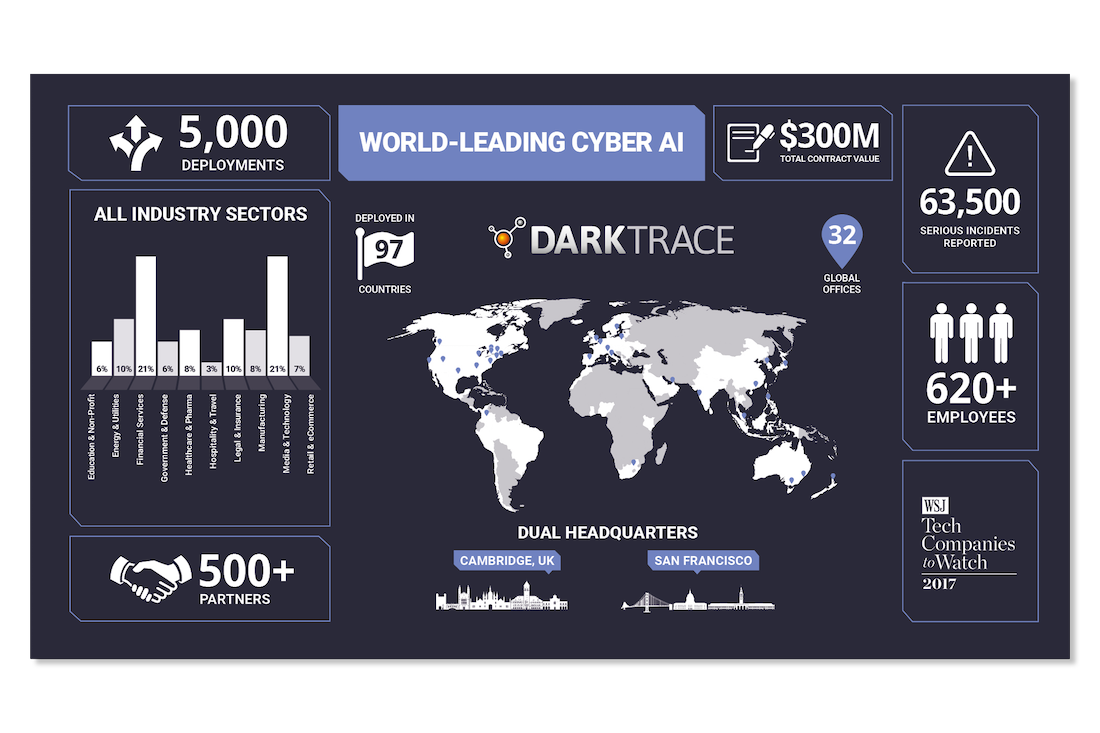
Who is Darktrace and where are they located?
What are the highlights regarding CYBER AI Platform Detection of the Immune System?
What is Autonomous Response and how can it help my business?
What is Darktrace Advance Search?
Darktrace analyzes network traffic through Deep Packet Inspection; each connection is processed and logs containing key metadata about the connection are produced. Similarly, Darktrace Security Modules and other integrations analyze activity data from third-party platforms and create log entries for each event. The Threat Visualizer interface displays a relevant subset of this metadata in device event logs and breach logs, however as an investigation progresses, the need can arise to review connections and events in more detail.
Why our customers want Darktrace protection?
The Advanced Search interface provides searchable access to the detailed metadata logs produced by network traffic and event analysis. For advanced users, complex query syntax and data aggregation analysis are available. For those just getting started, simple queries can be built up slowly and saved for future use.
Legacy Security Solutions If the initial breach is a simple, historical attack, it might be stopped. If it is one of the vast, ever-increasing number of sophisticated and novel attacks being launched, it can continue onto the next stage. Attackers will often purchase the off-the-shelf defenses to test their malware against to see if it will be effective. If the malware is brand new, it will likely pass these checks against all legacy solutions.
Darktrace’s Autonomous Response Breaches inherently break from a digital estate’s normal ‘pattern of life’ and can therefore be detected by Darktrace. Once detected, they are stopped at this early stage by Autonomous Response. This includes sophisticated attacks like spear phishing. Action taken is tailored and precise, meaning no disruption is suffered by the business. With Darktrace, ransomware attacks end here, but its Autonomous Response capabilities work at later stages as well.
Research shows that 80% of ransomware victims that pay the ransom suffer a second attack, often in the hands of the same group. The only way to truly keep the attackers from striking again is to know the full scope of the attack, ensure the attacker is no longer in your environment, and use a technology that doesn’t look at connections and events on a one-off basis. You need around the clock protection against machine attacks!
Will Darktrace offer similar Incident Response tactics?
Incident response Efforts are made to try to secure the vulnerabilities which allowed the attack to happen initially – the organization should be conscious that approximately 80% of ransomware victims will in fact be targeted again in the future. Legacy tools largely fail to shed light on the vulnerabilities which allowed the initial breach. Like searching for a needle in an incomplete haystack, security teams will struggle to find useful information within the limited logs offered by Firewalls and IDSs. Antivirus solutions may reveal some known malware but fail to spot novel attack vectors. Want to learn more?
Simply click the button below to watch the video regarding McLaren Automotive case study from Darktrace.